The IT Compliance topics that will be covered, are listed below:
HHS CLOUD COMPUTING Compliance
HIPAA Privacy Rule/Security Rule/Electronic Protected Health Information
HIPAA Privacy Rule protects the privacy of individually identifiable health information, called protected health information (PHI). The Security Rule protects a subset of information covered by the Privacy Rule, which is all individually identifiable health information a covered entity creates, receives, maintains or transmits in electronic form. The Security Rule calls this information “electronic protected health information” (e-PHI).
Entities that must abide by these rules include;
- Covered entities
- Business associates
A ‘covered entity’ is a health plan, a health care clearinghouse, or a health care provider who conducts billing and payment related transactions electronically
A ‘business associate’ is an entity or person, other than a member of the workforce of a covered entity, that performs functions or activities on behalf of, or provides certain services to, a covered entity that involve creating, receiving, maintaining, or transmitting PHI. A business associate also is any subcontractor that creates, receives, maintains, or transmits PHI on behalf of another business associate. A cloud computing firm, or any business providing cloud computing services, for these purposes, serves as a ‘business associate’.
When a covered entity engages the services of a Cloud Service Provider (CSP) to create, receive, maintain, or transmit ePHI (such as to process or store ePHI), on its behalf, the CSP is a business associate under HIPAA. Further, when a business associate subcontracts with a CSP to create, receive, maintain, or transmit ePHI on its behalf, the CSP subcontractor itself is a business associate.


Relevant Q&A
Q1. May a HIPAA covered entity or business associate use a cloud service to store or process ePHI?
Yes, provided the covered entity or business associate enters into a HIPAA-compliant business associate contract or agreement (BAA) with the CSP (in this case Synthys Medical) that will be creating, receiving, maintaining, or transmitting electronic protected health information (ePHI) on its behalf.
Q2. May a business associate of a HIPAA covered entity block or terminate access by the covered entity to the protected health information (PHI) maintained by the business associate of or on behalf of the covered entity?
Generally, No. However, arrangements may exist to dispose of (e)PHI, because of specific contractual obligations, completion of retention periods(see Q’s 7 & 8), or because of data aggregation. This data aggregation will generally render the source data, in the original format, as unreturnable to the covered entity. Any other outcome, such that the service level agreement (SLA) or business association agreement (BAA) with the Cloud Service Provider (CSP), or subcontractor of CSP, prevents the covered entity from accessing its ePHI, is a violation of Federal Law.
the terms of the SLA and BAA with the CSP do not prevent the entity from accessing its ePHI in violation.
Q3. If a Cloud Service Provider (CSP) stores only encrypted ePHI and does not have access to a decryption key, is it a HIPAA business associate?
Yes. In this capacity, the CSP that receives, maintains, processes, or stores ePHI, for a covered entity or another business associate, even if it cannot decipher the stored data, is a HIPAA business associate.
Q4. May a HIPAA covered entity (or business associate) use a Cloud Service Provider (CSP) to maintain ePHI without first executing a business associate agreement (BAA) with that CSP?
No. Doing so constitutes a violation of the HIPAA Rules and associated Federal Law. The HHS Office of Civil Rights (OCR) will investigate any complaint. Under the HITECH Act’s updates to HIPAA, the OCR will aggressively implement a resolution agreement and corrective action plan, which will always include serious financial penalties.
Q5. Do the HIPAA Rules allow health care providers to use mobile devices to access ePHI in a cloud?
Yes. Covered entities, healthcare providers, and business associates may do so, as long as required physical, technical, and administrative safeguards are in place. These, in total, must protect the confidentiality, integrity, and availability of ePHI. The HIPAA Rules do not endorse or require any specific type of technology, nor will they ever endorse specific vendors.
Q6. Do the HIPAA Rules allow health care providers to use email to transfer ePHI in the cloud?
Yes, but. The Security Rule specifies that the data must be ‘adequately protected.’ This reasonably suggests that encryption be utilized.
Q7. What is the minimum encryption level is specified in the HIPAA Security Rule for the transfer of data by email?
None through the Security Rule. However, the National Institute of Standards & Technology (NIST) recommends that a minimum Advanced Encryption Standard (AES) standard of 128 be applied, with AES 256 strongly encouraged.
Q8. Is a Cloud Service Provider(CSP) required to maintain ePHI for any period of time beyond when it has finished providing services to a covered entity or business associate?
No. The implemented business associate agreement (BAA) must specify that a CSP or related business associate must return or destroy all ePHI immediately before the termination of the BAA. The only ePHI which does not need to be returned, is component data that has been aggregated. This component data must, however be destroyed before the termination of the BAA.
Q9. Assume a Cloud Service Provider (CSP), or business associates is actively maintaining ePHI. What are the retention guidelines for retention of actively maintained ePHI?
ePHI (and all HIPAA data) must be maintained for six years from the date of its creation or the date when it last was in effect, whichever is later. HIPAA requirements supercede State laws if the state law specifies shorter periods. State law supercedes HIPAA if the state law requires a retention period longer than six years. This is actually specified in the HIPAA administrative rules, not the HIPAA Privacy Rule.
Q10. Assume a Cloud Service Provider(CSP) maintains only data that has been de-identified in accordance with the HIPAA Privacy Rule. Must that CSP execute a business associate agreement (BAA) with the source covered entity?
No. The Privacy Rule does not restrict the use or disclosure of de-identified information, nor does the Security Rule require that any safeguards be applied, given that de-identified information is not considered (e )PHI.
Q11. Are covered entities or business associates allowed to use a Cloud Service Provider(CSP) that stores ePHI on servers outside of the United States?
Yes. As long as the covered entity (or business associate) enters into a business associate agreement (BAA) with the Cloud Service Provider(CSP). Although the HIPAA Rules make no specific reference to storing data on servers outside of the US, it is assumed that the CSP, in concert with the covered entity and related business associates, have done a ‘risk analysis’ related to this specific situation, and finds the risks to be reasonable.
Q12. Are covered entities who have entered into signed BAA’s with Cloud Service Providers (CSP’s) allowed to ‘audit’ the security practices of the CSP?
No. The HIPAA Rules simply require that covered entities and business associates obtain strong assurances, in the form of a BAA, that the CSP will appropriately safeguard the ePHI it creates, receives, maintains, or transmits. The HIPAA Rules do not expressly demand that a CSP provide documentation of its security practices, but the drafted BAA may request the generation of safeguard documentation, and the results of internal audits created by the CSP for themselves.
Q13. Are there any HIPAA Security Rule requirements in place specifying how CSP’s must handle their audit logs?
Yes, indirectly. Audit logs may often include the names of patients, which is ePHI. Like all ePHI, the audit logs must be ‘adequately protected’ from release and unauthorized access.
Q14. A Cloud Service Provider(CSP) is storing my personal genetic information. Is this protected information(ePHI), requiring that a BAA be in place ?
Yes, of course. To be protected, it must meet the definition of protected health information: it must be individually identifiable and maintained by a covered health care provider, health plan, or health care clearinghouse.
HHS HIPAA Compliance
Overview
HIPAA compliance is, of course, a must for healthcare providers. HIPAA guidelines protect patients’ health information, guaranteeing it is stored securely, accessed only by those with need, and applied correctly. Data that can reveal a patient’s identity, called Patient Heath Information (PHI), must be kept confidential. HIPAA compliance is adherence to the physical, administrative, and technical safeguards outlined in HIPAA, which covered entities and business associates must uphold to protect the integrity of Patient Health Information (PHI).
The Five Main Directives of HIPAA
- HIPAA Title I focuses on the new insurance reform that was introduced in HIPAA, specifying rules about the access, portability, and renewability of health insurance. Making it possible to maintain coverage when your employment changes and making it unlawful for group insurance plans to turn down health coverage.
- HIPAA Title II concentrates on the required steps of the Privacy Rule, Security Rule, and the Enforcement Rule. It also defines national standards on how electronic healthcare transactions are processed by the U.S. Dept of Health and Human Services (HHS)
- HIPAA Title III introduces new tax rules related to healthcare treatment including the provisioning of certain deductions for medical insurance.
- HIPAA Title IV provides details on the reform of insurance law, with protections for those who have pre-existing conditions and individuals who want to maintain their insurance.
- HIPAA Title V gives guidelines for life insurance policies that are owned by businesses and how to handle income tax specifics when someone has their US citizenship revoked.



HIPAA and Information Technology/Cloud
Not surprisingly, a HIPAA compliant IT service provider will be most concerned with HIPAA Title II. Title II establishes and describes these five elements;
- National Provider Identifier Standard – 10-digit NPI (national provider identifier) numbers must be assigned to all healthcare entities.
- Transactions and Code Set Privacy Standard – this objectively approved protocol must be used in electronic data interchange (EDI).
- HIPAA Privacy Rule – Ensuring that Patient Health Information (PHI) is protected. The Privacy Rule is actually short-hand for the “Standards for Privacy of Individually Identifiable Health Information.”
- HIPAA Security Rule – This rule delineates expectations for the safeguarding of patient data. The Security Rule is short-hand for the “Security Standards for the Protection of Electronic Protected Health Information.”
- HIPAA Enforcement Rule – This subsection of the law provides parameters with which companies should be investigated for potential or alleged violations.
The HIPAA Privacy Rule, and HIPAA Security Rule will be reviewed next. The Security Rule includes three safeguards components;
- Technical safeguards
- Physical safeguards
- Administrative safeguards
HIPAA Privacy Rule
HIPAA’s Privacy Rule is in place to ensure that Patient Health Information (PHI) is protected. The Privacy Rule is actually called “Standards for Privacy of Individually Identifiable Health Information.”
- Prompt response – HIPAA legislation allows for a maximum of just 30 days to get back with responses to patient access requests. (Required)
- Notice of privacy practices – An NPP is required to officially inform patients and subscribers of data sharing policies. (Required)
- Privacy training – Medical personnel must be trained to recognize what data can and cannot be shared internally and externally. (Required)
- Ensure data is valid – “Ensure appropriate steps are taken to maintain the integrity of ePHI and the individual personal identifiers of patients,” instructs HIPAA Journal. (Required)
- Get authorization – Obtain permission from any and all patients to use redacted ePHI for research, fundraising, or marketing. (Required)
- Update documentation – All authorization forms should now include a reference to changes in the treatment of school immunizations, ePHI restriction in disclosure to health plans, and the right of patients to access their electronic records. (Required)
HIPAA Security Rule
The HIPAA Security Rule defines the requirements for the protection of electronic patient health information. The Security Rule refers to “Security Standards for the Protection of Electronic Protected Health Information.” These are ‘safeguards’, and there are three of them;
- Technical
- Physical
- Administrative
Technical safeguards;
- Network encryption – All ePHI must be encrypted so as to meet NIST cryptographic standards any time it is transmitted over an external network. (Required)
- Control access – Each user is assigned a centrally-controlled unique username and PIN code/password to access the systems. Procedures must also be in place to govern when to release or disclose ePHI if during an emergency. (Required)
- Authenticate ePHI – You must identify and authenticate ePHI and protect it from corruption, unauthorized changes, and accidental destruction. (Recommended)
- Encrypt devices – All end-point devices that access the system should be able to encrypt and decrypt data. Critical for mobile and laptop devices. (Recommended)
- Control activity audits – Detailed logging is needed to track all ePHI access attempts and to monitor how ePHI data is manipulated. (Recommended)
- Enable automatic logoff – Users must be auto logged out after a certain set time-frame, usually between 30 seconds and 3 minutes, based on the application or system. (Recommended)
Physical safeguards;
- Control facility access – Must carefully track the specific individuals who have physical access to data storage. This does apply to just health care workers or engineers, but also repair people and even custodians. A plan of action to block unauthorized entry must be developed. (Required)
- Manage workstations – A policy must be drafted that limits which computer workstations (and other devices) have access to health data, describes how a screen should be guarded from being viewed at a distance, and specifies appropriate workstation use. (Required)
- Remove mobile device ePHI– Define a mobile device policy that deletes ePHI before a device is transferred to another user. (Required)
- Track computer servers – Create an inventory of your server and device infrastructure, including current physical location. Before moving a server or device, data should be copied. (Recommended)
Administrative safeguards;
- Risk assessment – Identify, analyze and define risk elements and probabilistic outcomes. Complete a comprehensive risk assessment for all health data. Create and put into place action plans to resolve outcomes in line with the defined risk assessments. (Required)
- Systematic ongoing risk management – Risk assessment is an ongoing process that must be reviewed at regular intervals with recalibrated measures put in place to reduce the risks to an appropriate level. A sanctions policy must be introduced for employees who fail to comply with HIPAA regulations. (Required)
- Train staff – Employees need to be trained on all ePHI access protocols and on how to recognize potential cybersecurity risks such as phishing, hacking, and deception. A record of these sessions must be kept. (Recommended)
- Build contingencies – Implement ongoing business continuity, responding to potential disasters with a preparation process that keeps data safe. (Required)
- Test contingencies – Test contingency plan(s) on a regular basis, with relation to all key software. A backup system and restoration policy should be adopted. (Recommended)
- Block unauthorized access – Be certain that parties that haven’t been granted access, such as subcontractors or parent companies, cannot view ePHI. Sign business associate agreements with all partners. (Required)
- Document all security incidents – Note that this step is separate from the Breach Notification Rule, which has to do with actual successful hacks. A security incident can be stopped internally before data is breached. Staff should recognize and report these occurrences. (Recommended)
Major Changes to HIPAA Since Passage in 1996
There have been four major amendments since 1996:
- The Security Rule Amendment of 2003
- Technical Safeguards
- Physical Safeguards
- Administrative Safeguards
- The Privacy Rule Amendment of 2003
- The Breach Notification Rule of 2009
- The Final Omnibus Rule of 2013
We will focus on the Breach Notification Rule of 2009 next.
HIPAA Breach Notification Rule
HIPAA’s Breach Notification rule sets out requirements for notification contact and timing, in the event of a protected health data breach.
- Notification process; If a breach of ePHI occurs, both patients and the HHS Department must be alerted. If more than 500 patient records are involved, notification of local media is required. If less than 500 patients, execution/submission of a small-scale hack form through the OCR website if required. Smaller breach reports can be delayed, because OCR directives require that small scale breach reports only be made annually.(within sixty days of the close of the calendar year). Large scale breaches, trigger an immediate notifications including immediate contact of the HHS Secretary by the resident HIPAA CE. (Required)
- Four breach notification components; Each breach notification message contains four components;
-
- A description of the ePHI and personal identifiers involved in the breach
- Name of the party which gained unauthorized access to PHI or related information
- Distinction of whether ePHI details were visually seen vs removed – viewing vs. acquisition (if known)
- The degree to which risk mitigation has succeeded. (Required)
Consequences of Violating HIPAA Regulations
There are four levels of violations described by the HIPAA Enforcement Rule, with the fine range is in parenthesis;
- “Unaware based on reasonable measure” – The entity was unaware and would have remained unaware based on reasonable measures. ($100 to $50,000)
- “Reasonable cause” – in which the violation was caused by an element that would prompt action in an ordinary person. ($1000 to $50,000)
- “Willful neglect” – in which the violation was caused by intentional avoidance but rectified within 30 days. ( $10,000 to $50,000)
- “Willfull neglect not mitigated” – Willful neglect but not mitigated within 30 days. ($50,000)



What Does HITECH Have to Do With HIPAA Healthcare?
HITECH is the acronym associated with the Health Information Technology for Economic and Clinical Health Act of 2009. The legislation, signed into law by President Obama on February 17, was intended to accelerate the transition to electronic health records (EHR). It was actually included within the American Recovery and Reinvestment Act of 2009 (ARRA), which was geared toward stimulating the economy during the Great Recession.
The Office of the National Coordinator for Health Information Technology (ONC), part of the HHS Department since 2004, is responsible for the administration and creation of standards related to HITECH. Of course, HIPAA hosting providers deploying electronic health records must satisfy the EHR requirements defined by ONC, while simultaneously complying with the HIPAA Privacy and Security Rules. Effectively, HITECH is an addendum to HIPAA.



HHS HITECH Compliance
Overview
Healthcare organizations across the US understand the importance of the Health Insurance Portability and Accountability Act (HIPAA). HIPAA, and related legislation, however, has been a ‘moving target’. HIPAA has had a very positive impact, including prescribing and enforcing the protection and security of patient health records. Despite this, HIPAA has created a ‘mountain of work’ for health care providers to deliver on the requirements, and protect themselves from financial sanctions because of an ePHI breach.
HIPAA wasn’t always a complex piece of legislation. When introduced and signed by President Clinton in 1996, it was only 337 words. By 2002, however, HIPAA legislation had grown to over 100,000 words and 500 pages, and healthcare providers were buried. Many healthcare organizations needed to employ multiple individuals, at each site, just to keep track of new and changing requirements.
Before we move to a discussion of HITECH, which is the technology related legislation serving as an addendum to HIPAA, let’s review HIPAA Title II.
HIPAA and Information Technology/Cloud
Not surprisingly, a HIPAA compliant IT service provider will be most concerned with HIPAA Title II. Title II establishes and describes these five elements;
- National Provider Identifier Standard – 10-digit NPI (national provider identifier) numbers must be assigned to all healthcare entities.
- Transactions and Code Set Privacy Standard – this objectively approved protocol must be used in electronic data interchange (EDI).
- HIPAA Privacy Rule – Ensuring that Patient Health Information (PHI) is protected. The Privacy Rule is actually short-hand for the “Standards for Privacy of Individually Identifiable Health Information.”
- HIPAA Security Rule – This rule delineates expectations for the safeguarding of patient data. The Security Rule is short-hand for the “Security Standards for the Protection of Electronic Protected Health Information.”
- HIPAA Enforcement Rule – This subsection of the law provides parameters with which companies should be investigated for potential or alleged violations.
The HIPAA Security Rule will be reviewed below. (For a review of the Privacy Rule and the Enforcement Rule, and penalties for violating HIPAA, please go here; HHS HIPAA Compliance
The Security Rule includes three safeguards components;
- Technical safeguards
- Physical safeguards
- Administrative safeguards
HIPAA Security Rule
The HIPAA Security Rule defines the requirements for the protection of electronic patient health information. The Security Rule refers to “Security Standards for the Protection of Electronic Protected Health Information.” These are ‘safeguards’, and there are three of them;
- Technical
- Physical
- Administrative
Technical safeguards;
- Network encryption – All ePHI must be encrypted so as to meet NIST cryptographic standards any time it is transmitted over an external network. (Required)
- Control access – Each user is assigned a centrally-controlled unique username and PIN code/password to access the systems. Procedures must also be in place to govern when to release or disclose ePHI if during an emergency. (Required)
- Authenticate ePHI – You must identify and authenticate ePHI and protect it from corruption, unauthorized changes, and accidental destruction. (Recommended)
- Encrypt devices – All end-point devices that access the system should be able to encrypt and decrypt data. Critical for mobile and laptop devices. (Recommended)
- Control activity audits – Detailed logging is needed to track all ePHI access attempts and to monitor how ePHI data is manipulated. (Recommended)
- Enable automatic logoff – Users must be auto logged out after a certain set time-frame, usually between 30 seconds and 3 minutes, based on the application or system. (Recommended)
Physical safeguards;
- Control facility access – Must carefully track the specific individuals who have physical access to data storage. This does apply to just health care workers or engineers, but also repair people and even custodians. A plan of action to block unauthorized entry must be developed. (Required)
- Manage workstations – A policy must be drafted that limits which computer workstations (and other devices) have access to health data, describes how a screen should be guarded from being viewed at a distance, and specifies appropriate workstation use. (Required)
- Remove mobile device ePHI– Define a mobile device policy that deletes ePHI before a device is transferred to another user. (Required)
- Track computer servers – Create an inventory of your server and device infrastructure, including current physical location. Before moving a server or device, data should be copied. (Recommended)
Administrative safeguards;
- Risk assessment – Identify, analyze and define risk elements and probabilistic outcomes. Complete a comprehensive risk assessment for all health data. Create and put into place action plans to resolve outcomes in line with the defined risk assessments. (Required)
- Systematic ongoing risk management – Risk assessment is an ongoing process that must be reviewed at regular intervals with recalibrated measures put in place to reduce the risks to an appropriate level. A sanctions policy must be introduced for employees who fail to comply with HIPAA regulations. (Required)
- Train staff – Employees need to be trained on all ePHI access protocols andon how to recognize potential cybersecurity risks such as phishing, hacking, and deception. A record of these sessions must be kept. (Recommended)
- Build contingencies – Implement ongoing business continuity, responding to potential disasters with a preparation process that keeps data safe. (Required)
- Test contingencies – Test contingency plan(s) on a regular basis, with relation to all key software. A backup system and restoration policy should be adopted. (Recommended)
- Block unauthorized access – Be certain that parties that haven’t been granted access, such as subcontractors or parent companies, cannot view ePHI. Sign business associate agreements with all partners. (Required)
- Document all security incidents – Note that this step is separate from the Breach Notification Rule, which has to do with actual successful hacks. A security incident can be stopped internally before data is breached. Staff should recognize and report these occurrences. (Recommended)
Please note – these elements were all defined before the creation of HITECH.



HITECH As An Addendum to HIPAA
HITECH is the acronym associated with the Health Information Technology for Economic and Clinical Health Act of 2009. The legislation, signed into law by President Obama on February 17, 2009, was intended to accelerate the transition to electronic health records (EHR). It was actually included within the American Recovery and Reinvestment Act of 2009 (ARRA), which was geared toward stimulating the economy during the Great Recession.
The Office of the National Coordinator for Health Information Technology (ONC), part of the HHS Department since 2004, is responsible for the administration and creation of standards related to HITECH. Of course, HIPAA hosting providers deploying electronic health records (EHR) must satisfy the requirements defined by ONC, while simultaneously complying with the HIPAA Privacy and Security Rules. Effectively, HITECH is an addendum to HIPAA.
Electronic Health Record & Meaningful Use
The HITECH Act included the concept of electronic health records – meaningful use [EHR-MU], an effort led by Centers for Medicare & Medicaid Services(CMS) and the Office of the National Coordinator for Health IT (ONC). HITECH proposed the meaningful use of interoperable electronic health records throughout the United States health care delivery system as a critical national goal.
Meaningful Use(MU) was defined by the following two components;
- use of certified EHR technology in a meaningful manner (for example electronic prescribing)
- ensuring that certified EHR technology connects in a fashion that provides for the electronic exchange of health information to improve the quality of care.
By using certified EHR technology(CEHRT), the provider has agreed to submit to the Secretary of Health & Human Services (HHS) information on the quality of care and other measures. The concept of Meaningful Use(MU) rested on the five(5) key components of health outcomes policy priorities, namely:
- Improving quality, safety, efficiency, and reducing health disparities
- Engage patients and families in their health
- Improve care coordination
- Improve population and public health
- Ensure adequate privacy and security protection for personal health information
Historically, the Meaningful Use directive has consisted of three stages:
- Stage 1 established the basis by establishing requirements for the electronic capture of clinical data, including providing patients with electronic copies of health information.
- Stage 2 expanded upon the Stage 1 criteria with a focus on advancing clinical processes and ensuring that the meaningful use of EHRs supported the aims and priorities of the National Quality Strategy. Stage 2 criteria encouraged the use of Certified Electronic Health Record Technology (CEHRT) for continuous quality improvement at the point of care and the exchange of information in the most structured format possible.
- In October 2015, CMS released a final rule that established Stage 3 in 2017 and beyond, which focused on using CEHRT to improve health outcomes.
Quality Payment Program (QPP) Precursor – Sustainable Growth Rate (SGR)
Prior to the Quality Payment Program (QPP), payment increases for Medicare services were set by the Sustainable Growth Rate (SGR) law. This capped spending increases according to the growth in the Medicare population, and a modest allowance for inflation. However, as clinicians increased their utilization of services, the reimbursement for each unit of service had to be adjusted downward to hold costs constant. As a result, the SGR would have resulted in large decreases in the Physician Fee Schedule, which was not sustainable. To avoid these decreases in reimbursement, Congress had to pass a new law every year authorizing the current fee schedule and a small increase for inflation.
The Quality Payment Program (QPP) Became Operational January 1, 2017.
In 2015, Congress passed the Medicare Access and CHIP Reauthorization Act of 2015 (MACRA). This law eliminated SGR, and replaced it with the Quality Payment Program. The new focus is to reward high-value, high-quality Medicare providers with payment increases, while at the same time reducing payments to those providers who aren’t meeting performance standards.
Of course, without the implementation of Certified Electronic Health Record Technology (CEHRT), the QPP would have been impossible, given the missing electronic health records which server as the basis for QPP metrics.
Clinical providers now have two tracks to choose from, as defined in the Quality Payment Program based on their practice size, specialty, location, or patient population:
- Merit-based Incentive Payment System (MIPS) or
- Advanced Alternative Payment Models
MIPS goes into effect based on minimum threshold volumes (patients and dollars charged to CMS). The advanced APM is a track of the Quality Payment Program that offers a 5 percent incentive for achieving threshold levels of payments or patients.
PCI -DSS Compliance
What is PCI?
The PCI (Payment Card Industry) is a sector within the financial industry that is responsible for all electronic payments. As purchases are executed through debit, credit, ATM, POS, and prepaid systems, sensitive financial data is constantly transmitted to different parts of the world. Given the vast financial values involved, strict security measures must be in place in order to protect all users engaging in non-cash exchanges of payment.
What is PCI-SSC ?
To create these standards, the major financial corporations developed the PCI-SSC (Payment Card Industry Security Standards Council) which stands as an independent entity from the top financial firms in the US and Japan. The council attempts to protect cardholders by setting strict security standards for merchants and for vendors of payment-processing solutions.
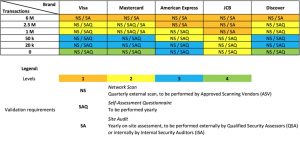
The PCI Security Standards Council is a global forum for the ongoing development, enhancement, storage, dissemination, and implementation of security standards for account data protection. The Standards Council was established by the major credit card associations (Visa, MasterCard, American Express, Discover, JCB) as a separate organization to define appropriate practices that merchants and service providers should follow to protect cardholder data. It is this council of companies that created the Payment Card Industry (PCI) Data Security Standards (DSS).
What is PCI DSS ?
Credit and debit cards fuel most global commerce transactions. By definition, they are also a lucrative targets for fraudsters. To protect cardholder data, merchants and vendors must adhere to the Payment Card Industry Data Security Standard (PCI DSS), which establishes a baseline level of security for organizations that store, process, or transmit payment card data.
The PCI Data Security Standard has grown significantly in stature and coverage since its early beginnings. PCI DSS requirements are potent and comprehensive. Any organizations that invests the time and effort to comply with them will be dramatically more secure and protected from cybersecurity threats.

Who Must Comply with PCI DSS ?
The term “standard” in the PCI Data Security Standard could lead merchants to incorrectly conclude that implementation of PCI compliance requirements is “voluntary” or “good to have” rather than a requirement. In reality, PCI DSS is effectively an ironclad requirement/regulation. Any merchant that attempts to process a credit card, issued by a member organization, without having implemented PCI-DSS, will likely be subject to a large fine. This fine will be levied shortly after the merchant is barred from processing any transactions. So, unless a merchant is planning to run a “cash only” business, the PCI-DSS Standard and related certification is not optional.

What are the PCI DSS Requirements (Control Objectives) ?
Control Objectives – PCI DSS Requirements
PCI compliance requirements are built around six “control objectives,” and each of these objectives has sub-requirements that organizations must follow. A total of 12 compliance sub-requirements complement the six control objectives. The summary may be found below:
1. Build and Maintain a Secure Network
- a. Install and maintain a firewall configuration to protect cardholder data.
- b. Do not use vendor-supplied defaults for system passwords and other security parameters.
2. Protect Cardholder Data
- a. Protect stored data.
- b. Encrypt transmission of cardholder data across open, public networks.
3. Maintain a Risk/Vulnerability Management Program
- a. Use and regularly update anti-virus software.
- b. Develop and maintain secure systems and applications.
4. Implement Strong Access Control Measures
- a. Restrict access to cardholder data by business need-to-know.
- b. Assign a unique ID to each person with computer access.
- c. Restrict physical access to cardholder data.
5. Establish a Comprehensive Monitoring Solution
- a. Track and monitor all access to network resources and cardholder data.
- b. Regularly test security systems and processes.
6. Maintain an Information Security Policy
- a. Maintain a policy that addresses information security.
Expanded Review of Requirements (Prescriptive)
- Protect your cardholder data with firewalls. Firewalls are designed to block inbound and outbound network traffic from untrusted networks.
- Change vendor-supplied default passwords and configurations. These defaults are freely published online and available for hackers to misuse.
- Protect cardholder data at rest using strong encryption, hashes, and/or other methods that are part of industry-accepted best practices.
- Protect cardholder data in transit using strong encryption, trusted keys, and trusted digital certificates.
- Use anti-virus and anti-malware software to protect all systems, and keep it fully updated at all times with the latest patches and signatures.
- Establish a process to identify vulnerabilities in systems and applications so that they can be remediated expeditiously.
- Restrict all access to cardholder data by employing the principles of least privilege and “need to know.”
- Assign a unique ID to each individual with access to systems and applications so that complete accountability of access is in place.
- Use electronic access keys, surveillance and other security measures to restrict physical access to cardholder data and cardholder data systems.
- Establish a logging and monitoring mechanism to track access and user activities related to cardholder data and cardholder network resources.
- Perform annual penetration tests and comprehensive risk assessments on the cardholder data environment. Perform quarterly vulnerability scans.
- Draft, maintain, and disseminate a comprehensive data security policy and update it annually or whenever there is a significant change in the technological/operational
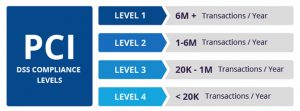
How Does the Transaction Volume Impact PCI-DSS Compliance?
PCI compliance requirements applicable to a merchant/organization are highly dependent on how many credit, debit and pre-paid card transactions are processed by them each year. The greater the number of transactions, the higher the level of required compliance and compliance validation. Two use cases next;
- More than 6 million transactions per year; merchant must hire a specially trained assessor (PCI QSA) to conduct an audit every year.
- Less than 6 million transactions per year; merchants may not required to perform an audit, but must perform quarterly network scans to look for signs of trouble.
As we will see below, there are exceptions triggering an audit requirement, for transactions less than six million (see Four PCI-DSS Compliance Levels, Based on Transaction Volume, & Source Vendor ). Both American Express and JCB (Japan Credit Bank) trigger Site Audits at lower transaction levels, than Visa, Mastercard, or Discover.
What are the Four PCI Transaction Levels?
- Level 1: > 6 milion transactions/year
- Level 2: 1 million to 6 million transactions/year
- Level 3: 20,000 to 1 million transactions/year
- Level 4: < 20,000 transactions/year
What are the Major Possible Components of PCI DSS Compliance, and the Deliverable Form?
- Self-Assessment Questionnaire (SAQ)
- Attestation of Compliance
- Quarterly Network Scans
- Report on Compliance
- Annual Audit
- Special Situations & Elevated Compliance Requirements
When Do I Need to Select a PCI QSA Firm ?
When an annual audit is required for PCI DSS compliance, it must be performed by a Payment Card Industry Qualified Security Assessor (PCI QSA) company. A PCI QSA is certified by the PCI Security Standards Council to audit merchants for PCI DSS compliance.
The PCI Security Standards Council maintains a list of all the individuals and companies that have successfully completed training and certification as a PCI QSA.
A PCI compliance audit automatically applies to PCI level 1 compliance entities – those with more than 6 million transactions/year.
Organizations that must complete a self-assessment questionnaire (SAQ) can voluntarily request the assistance of a PCI QSA firm. Voluntary interaction with a competent PCI QSA company can assist a merchant in becoming more cognizant of compliance requirements in the light of business/operational goals. The PCI Security Standards Council website provides a list of certified PCI QSAs.
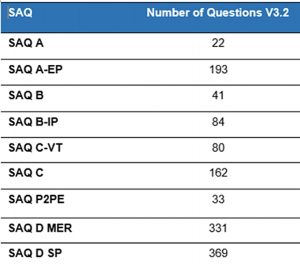
What is a SAQ? How Many Different Types of SAQ’s are There ?
A SAQ is a self-assessment questionnaire. There are eight of them, below.
- A: Card-not-present merchants (mail/telephone-order or e-commerce) who have completely outsourced all cardholder data processing to a third-party vendor and do not store, process or transmit any cardholder data on their systems or premises
- A-EP: E-commerce merchants who partially outsource all payment processing to a PCI DSS compliant firm.
- B: Merchants who do not store any electronic cardholder data and process payments either via standalone terminals.
- B-IP: Merchants who process online payments using only standalone , PTS-approved payment terminals.
- C: Merchants with payment application systems connected to the Internet and no electronic cardholder data storage.
- C-VT: Merchants who externally host a web payment application hosted by a PCI DSS validated third-party service provider. These types of merchants use a virtual payment terminal solution with no electronic cardholder data storage.
- D: Merchants not included in descriptions for the above SAQ types. Applicable to all service providers defined by a payment brand as eligible to complete an SAQ.
- P2PE: Merchants who process card data only via payment terminals included in a validated and PCI SSC-listed Point-to-Point Encryption (P2PE) solution. No electronic cardholder data storage.
For each of the eight(8) Self-Assessment Questionnaires(SAQ’s), the number of questions to be answered may be found below; { Note that D has been divided into two categories below }
HITRUST CERTIFICATION
Overview
HITRUST is a not-for-profit organization whose mission is to champion programs that safeguard sensitive information and manage information risk for organizations across all industries and throughout the third-party supply chain. It maintains the Common Security Framework(CSF). This CSF is an emerging standard, primarily in the health care industry, but applicable to the commercial space also. As a certifiable framework, it brings together multiple other compliance frameworks, such as;
- HIPAA: Health Insurance Portability and Accountability Act
- HITECH: Health Information Technology for Economic and Clinical Health
- NIST: National Institute of Standards and Technology
- ISO: International Organization for Standardization
- COBIT: Control Objectives for Information and Related Technology
- FTC: Federal Trade Commission
- PCI-DSS: Payment Card Industry Data Security Standard
- GDPR: General Data Protection Regulation (European Union)
By simultaneously addressing the security/process frameworks of HIPAA, HITECH, NIST, ISO, COBIT, FTC, PCI-DSS, and GDPR, HITRUST helps covered entities meet information security regulations across this broad interlocking set of security/compliance domains. This comprehensive deliverable is accomplished via one(1) unified compliance exercise. HITRUST also scales controls according to the type, size, and complexity of an organization.
From another perspective, HITRUST develops, maintains and provides broad access to its widely adopted common risk and compliance management and;
- de-identification frameworks
- related assessment and assurance methodologies, and
- initiatives advancing cyber sharing, analysis, and resilience
HITRUST incorporates HIPAA requirements and the NIST framework into a more prescriptive manner. Like ISO 27001 and FedRAMP, HITRUST certifies third-party auditors who can then grant an official certification of compliance to an organization. In addition to third-party certifications, both HIPAA and HITRUST have self-assessments that can be used to verify compliance with those standards.
What is HITRUST Compliance Certification?
Part of what makes HITRUST different is the fact that it is certifiable. A health care facility cannot be certified in HIPAA compliance or in how well the practice follows Federal Trade Commission laws. Customarily, healthcare practices just sign agreements that ‘verify’ that they are, in fact, HIPAA compliant. The applicable signed forms confirm that the healthcare practice has implemented the right measures to put security controls in place. Effectively, this cannot be confirmed or judged by anyone, making it more of an “I promise” sort of situation.
By moving to the HITRUST superset compliance methodology, the medical practice has two options for certification;
- Hire a HITRUST CSF assessor to execute the readiness exercise/validation assessment.
- Use the HITRUST self-assessment tool, which is very detailed and prescriptive in nature.
The self-assessment tool needs to be executed on a regular basis.
The HITRUST certification, whether obtained from a CSF assessor or via the self-assessment process, is good for two(2) years.
The CSF framework and HITRUST assessment and certification covers 19 different domains:

- Healthcare Data Protection & Privacy
- Information Protection
- Wireless Protection
- Transmission Protection
- Network Protection
- Endpoint Protection
- Portable Media Security
- Mobile Device Security
- Third Party Security
- Physical & Environmental Security
- Configuration Management
- Vulnerability Management
- Password Management
- Incident Management
- Risk Management
- Access Control
- Audit Logging & Monitoring
- Education, Training & Awareness
- Business Continuity Management & Disaster Recovery

HITRUST vs HIPAA
Let’s summarize with five important points;
- HITRUST is a superset of HIPAA and HITECH
- A medical practice cannot become HIPAA/HITECH certified
- A medical practice can become HITRUST (CSF) certified, via;
4. Assessment can be accomplished via;
Hiring of a HITRUST CSF assessor, who performs the assessment, OR Use the HITRUST self-assessment tool.
5. The HITRUST certification, whether obtained from a CSF assessor or
via the self-assessment process, is good for two(2) years.
FDA Dietary Supplements
&
Good Manufacturing Practice(GMP)

Certification of Dietary Supplements
FDA & NSF Involvement
Q&A
Q1: Who ensures the safety dietary supplements In the US?
Supplement manufacturers are responsible by law to ensure that their products are safe before being marketed. In addition, manufacturers are responsible for determining the accuracy and truth of label claims. However, the US Food and Drug Administration (FDA) can take action against:
- any unsafe dietary supplement product that reaches the market
- as well as any false or misleading claims

Q2: How does regulation of supplements differ from that of prescription or over-the-counter drugs?
Before sales and distribution, drugs must undergo clinical studies to determine their effectiveness, safety, possible interactions with other substances and appropriate dosages. FDA then reviews this data and determines whether to authorize use of the drugs. Dietary Supplements fall under the general category of food products. Unless they contain a new ingredient, dietary supplements are not tested or authorized for use prior to being marketed. Please note that the FDA has oversight over these products and can limit the type of ingredients used in product formulations and take action when false or misleading label claims are made.
Q3: How many different levels of certification are there for dietary supplements?
Currently two. For the first level, NSF International provides GMP (Good Manufacturing Practice) registration for companies. This requires a manufacturer to bring the NSF organization into the firm’s production sites, to validate that the manufacturer is following the GMP’s defined for their respective industry.
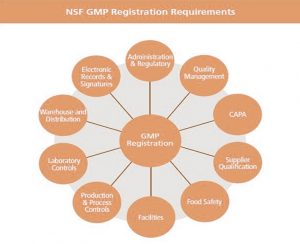
At each facility, there are customarily two NSF auditor visits a year. This certification is not a product certification, but ensures that companies follow best-practice procedures for:
- production and process control systems,
- personnel,
- physical plant and grounds,
- equipment and utensils,
- storage and distribution,
- etc.
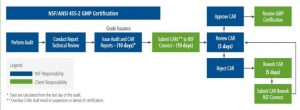
This GMP certification ensures a product has the identity, strength, composition, quality and purity that appears on its label. These GMP requirements are listed in Section 8 of NSF/ANSI 173. This is the only accredited American National Standard in the dietary supplement industry developed in accordance with the U.S. FDA’s 21 CFR part 111.
The second level involves certification in accordance with NSF/ANSI 455, which is an expanded certification and transition from the original NSF/ANSI 173 (section 8) GMP. (Please note that standalone warehouse and distribution facilities will remain under NSF/ANSI 173 GMP for the foreseeable future.)
The newer NSF/ANSI 455 standards was issued in January 2019, by the Global Retailer and Manufacturer Alliance (GRMA) . NSF/ANSI 455 is a set of consensus-based Good Manufacturing Practices (GMP) requirements for manufacturers of:
- dietary supplements (NSF/ANSI 455-2),
- cosmetics and personal care products (NSF/ANSI 455-3) and
- over-the-counter drugs (NSF/ANSI 455-4 ).
There are major changes in NSF/ANSI 455, in comparison to the original:
- Approved document contents/format
- Audit Grade Rules
- Post Audit Deadlines and Corrective Action Requests (CAR’s)
Approved Document Contents/Format
The new NSF/ANSI 455-2 GMP document set can be seen to the right. The original NSF GMP document standard may be seen to the right above.
The new standard maintains only seven document sets, whereas the original standard maintained ten.
Audit Grade Rules
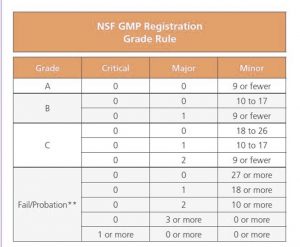
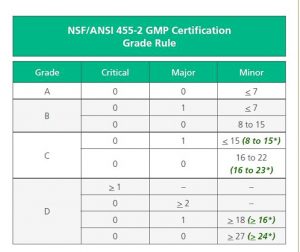
The Audit Grade Rules have changed significantly from the original NSF GMP Registration, to the NSF/ANSI 455-2 standard. Major changes include the following;
- A reduction in minor infractions from 9 to 7, in order to obtain an ‘A’ grade.
- A reduction in minor infractions from a maximum of 17 to a maximum of 15 to maintain a ‘B’ grade.
- A removal of the two major infraction option from the ‘C’ grade.
- A removal of three or more major infractions as an option for a ‘D’ grade.
*
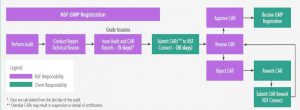
Post Audit Deadlines and Corrective Action Requests (CAR’s)
A very major change for Corrective Action Requests (CAR’s) has been implemented as the result of the transition from NSF GMP to NSF/ANSI 455-2 .
Specifically, the number of days allowed to submit Corrective Action Requests (CAR’s) back to NSF has dropped dramatically from 30 to 10.
Deadline to Move from NSF GMP to NSF/ANSI 455-2 GMP
.NSF started performing audits consistent with NSF/ANSI 455-2 GMP Certification in ovember 2019. The current timetable for transition is as follows:
- Through December 31, 2021 – Clients can select audits to NSF GMP Registration or NSF/ANSI 455-2 GMP Certification.
- After December 31, 2021 – NSF GMP Registration audits will be retired and replaced with NSF/ANSI 455-2 GMP Certification.
- Standalone Warehouse & Distribution facilities will remain under the original NSF GMP Registration program for the foreseeable future.



We WILL deliver the solution that you need !
As a first step, we will be delighted to answer any and all of your questions !